MAZE - How I would build AGI
Update: This is the first article in the MAZE machine learning series. You can read other articles here:
I can’t believe I am publishing this. I’ve been thinking about Artificial general intelligence and how to build it for a very long time. Call me crazy if you want, but I have an idea of building it differently from the mainstream approach. Instead of using backpropagation hammering down on smartly handcrafted networks, I want to build a system that can produce arbitrary neuron networks based on evolving and mutating genes in a series of controlled environments. Of course, every cool approach deserves an awesome acronym name. That’s why I named it MAZE (Massive Argumented Zonal Environments) 😎:

MAZE stands for Massive Argumented Zonal Environments
I spent last week building a prototype that can generate random neuron networks based on a gene sequence. Shockingly, I haven’t even implemented the part of generating offspring and gene mutation, but some randomly generated networks I saw during the development have already shown better performance than the ones I crafted manually during the learning process.
...
Read the full articleESP32 Tesla dashcam remote USB project in Rust failed. Here's what I've learned
As engineers, we all celebrate successful projects. But what about those that failed? Should we sweep them under the rug and pretend they never happened? There’s nothing wrong with a failed project. It’s not a shame but just part of the normal process to succeed. As long as we can learn from our mistakes and the lessons that come out of them, it’s a positive result. Today, I would like to share the story of my recent failed pet project – an ESP32-based Tesla dashcam video remote access system written in Rust.
The needs
It’s great being a Tesla driver that the dashcam system keeps recording, so if there’s any situation that happened, you have evidence to prove it. However, the video clips are on a USB drive. When you get home, if you want to pull out the clips, you need to unplug the USB drive, plug it into your computer, and copy the files you want. I always wish to have a USB thumb drive connecting to my home Wifi to make it possible for me to grab video files over the network without the manual process. A meme pops up in my mind to explain why you need a system like that.

A crying woman claimed: You hit my car and run 3 years ago. A guy replied: No, I didn't, here's the evidence
...
Read the full articleMy Beancount books are 95% automatic after 3 years
I am a big believer in building products for your needs, eating your own dog food, and finding customers with the same needs. Therefore, I started building BeanHub. Three years later, my Beancount books are 95% automatic, and I am a very happy user of my product. It’s hard to describe; as a computer nerd obsessed with automation, seeing my accounting book updating itself without me touching it in an open format brings me pure joy 😍
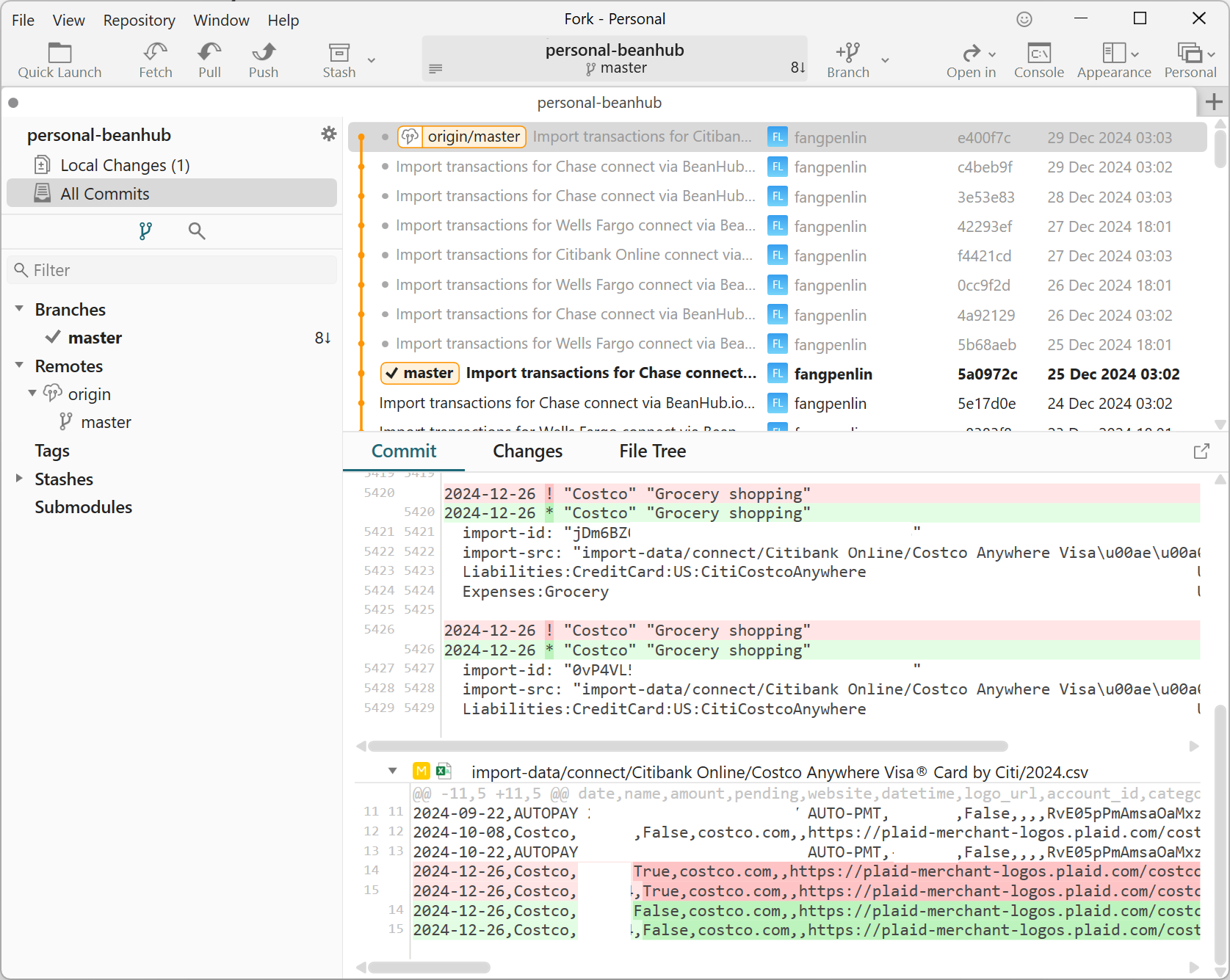
Screenshot of Git history and difference showing Beancount and bank transaction CSV files changes
Do you see this git commit of the Costco transaction turning from pending to confirmed? Yep! It’s all automatic, yet it’s just a Beancount file that can be read by any open-source Beancount tool! The better part is that other people are paying me, which is growing.
Today, I saw the unfortunate news about the shutting down of the beloved accounting software Bench on X.
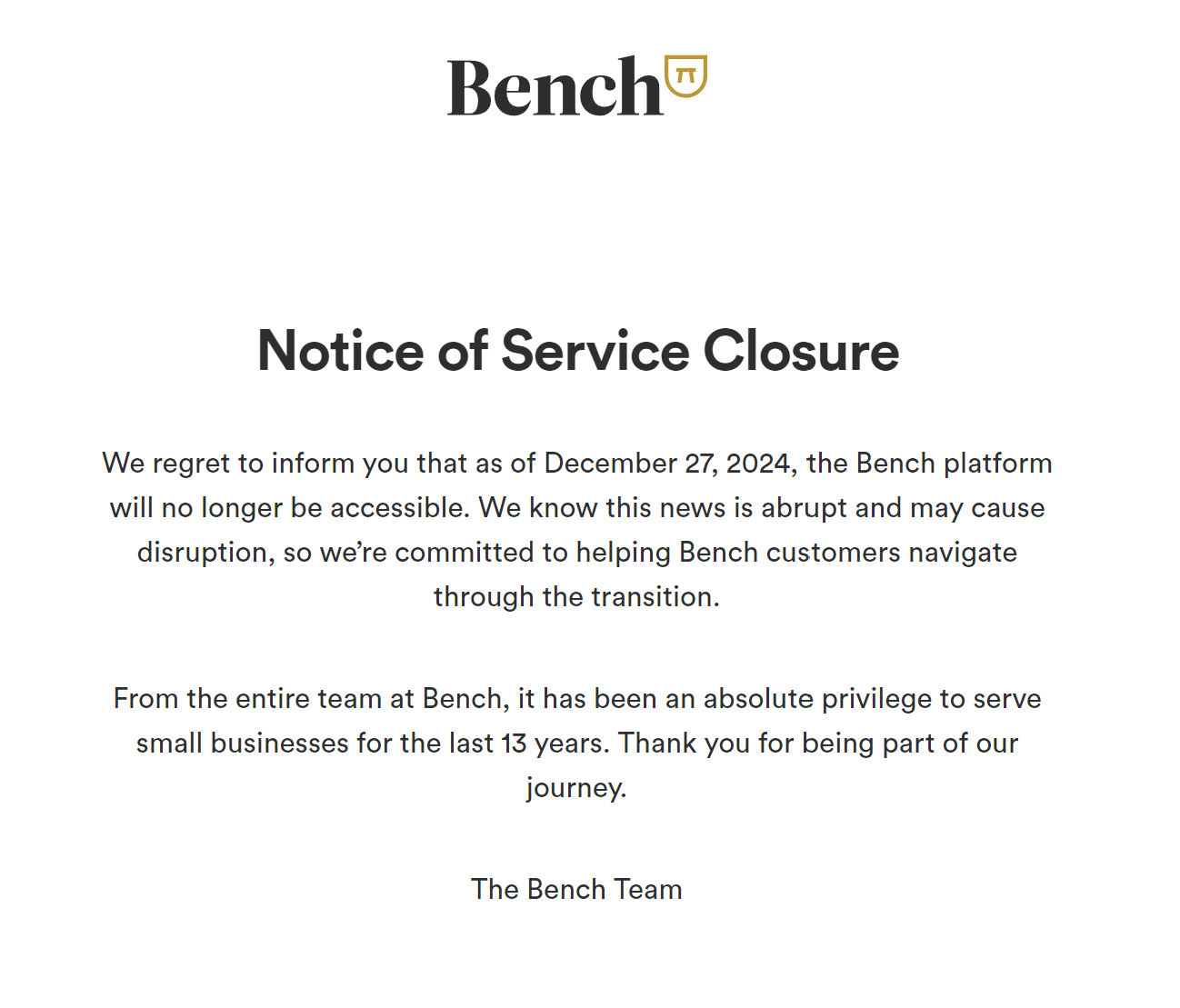
Shutdown notice of Bench accounting software
I am surprised, but I am not that surprised. Looking back now, I am really glad that I picked the rough road to build the product for myself. It doesn’t bring me financial freedom (yet), but at least I am a happy user myself, and I already have some paying customers. It’s not easy, though; it took me three years to get here, and I have overcome many interesting technology challenges and learned a lot from building it. Today, I would like to share my journey of building and selling BeanHub as a product.
...
Read the full articleCADing and 3D printing like a software engineer, part 1 - baby step with an overengineered webcam raiser
Like many of you nerds, a nerd like me when I was a little kid, I enjoyed tearing down stuff, putting it back together, and ensuring it worked. Somehow, I naturally desire to understand how things work and build stuff. One of my favorite books is The Way Things Work:

The Way Things Work book cover image
Highly recommended, by the way.
Just tearing down things and putting them back cannot contain my desire to build stuff at some point, so I became obsessed with programming. Over the decades, I felt very comfortable building things in the virtual world, but it’s becoming too comfortable. For now, I have the confidence to build almost any large-scale complex software system from the ground up by myself or with a team. Nevertheless, I still want to build something I can touch in the real world.
However, building things in the real world is challenging because the real world is messy, unlike the virtual world, which is usually binary. Although I don’t hate handcrafting stuff, there needs to be a significant improvement in the translation from idea to reality. Time consumption is also an essential factor. That all changed after 3D printers became more and more popular. You can print things as you designed. However, the problem with 3D printers is that I have heard that there are so many problems when you try to print something with it. I don’t want to spend most of my time troubleshooting printing problems; I want something that just works and focuses on design and iterations.
As you can see from my previous article, I built a mini-PC-based bare metal Kubernetes cluster with USB4 as the high-speed networking interface. Since then, the cluster has been sitting on the corner of the floor in my office, and it organically extended with different devices and got a bit messy over time. Cooling is also a concern because the three nodes stack together. There needs to be more room for good ventilation.
To improve the situation for my cluster, I had the idea of using a 3D printer to build my modular mini server rack. A while back, I realized that the 3D printers community recommends printers from Bambu Lab a lot. Most of them claimed it’s finally out-of-box and print. Then I wondered
Okay, maybe it’s the time. Let me build this! 🤔
However, since the money-saving spirit is hardwired in my DNA, I’m always jealous of YouTubers who get free stuff to review. Old school dinosaurs like me, who only write articles instead of making fancy videos, wondered why not ask them for sponsorship of my mini PC server rack project. So I asked. And YES, today I am happy to announce that this article is sponsored by … um…. nobody but myself once again!
So yeah, no, they didn’t reply 😂
Okay, fine. Who am I to ask for a sponsorship from? Since then, I have buried the idea deep down in my mind until recently, when I saw there’s a black Friday discount. Given that they aren’t sponsoring my tiny project, I have no choice but to punish them with money. So I did. Sorry, just being salty.

Since then, I have printed some little stuff and learned a little about CAD (Computer-aided Design). Surprisingly, my software engineer experience could translate into CAD. Today, I would like to share my experience of playing with 3D printers and also learning CAD from a software engineer’s perspective. This would be a series of articles sharing my experience moving toward the goal of building my cluster’s modular server rack. Hope you will like it, and here we go!
...
Read the full article